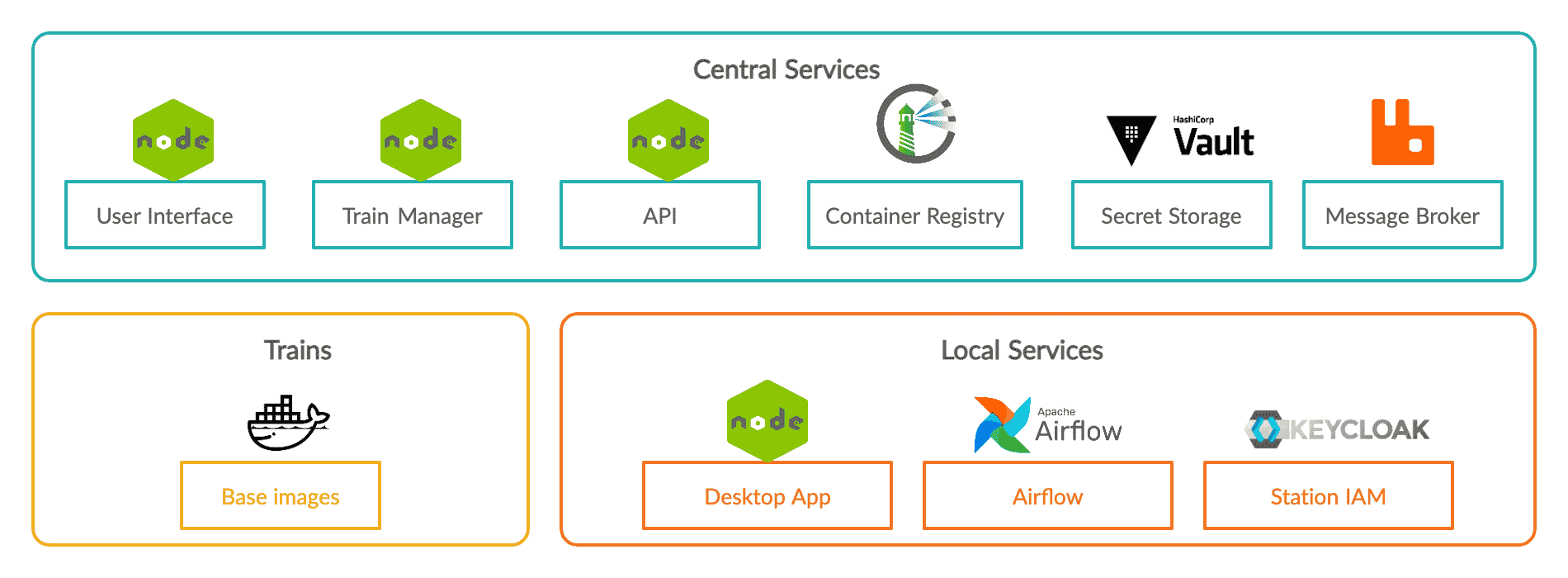
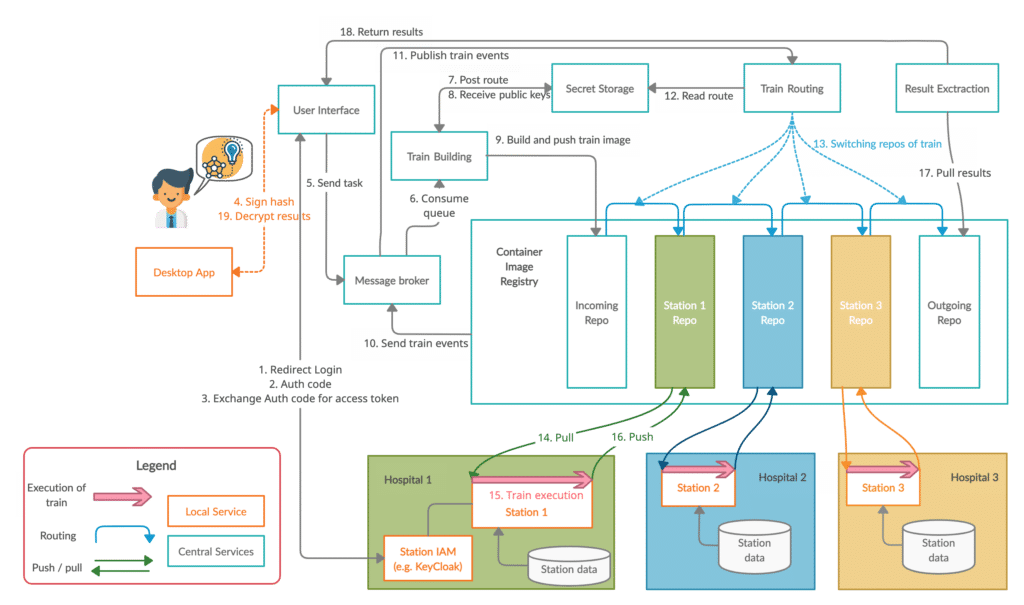
PHT-meDIC architecture components
Overall Workflow
- User is redirected to associated hospital local IAM
- Send Auth Code to UI
- Exchange Auth code for access token
- Sign hash from files during train submission
- UI sends building message to Message Broker
- Train Building receives message queue
- Post route of train to Vault
- Receive public keys of stations
- Build train and push in incoming repository
- Send event for incoming train
- Publish train event to Train Routing
- Receive route of train in Vault
- Move trains according to route and execution status
- Pull image
- Execute train at station locally
- Push executed train with encrypted results
- Result extraction of executed trains
- Return encrypted results
- Decrypt results locally with Desktop App
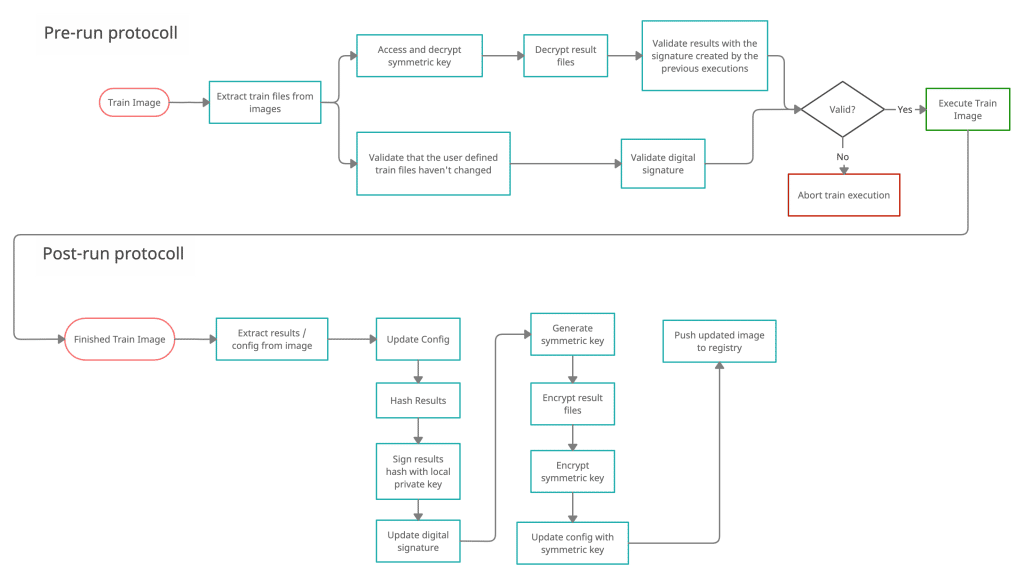
Execution at stations
The execution of a train is separated in 3 Phases:
- Pre-run protocol
- Container execution
- Post-run protocol
During first phase a validation check for manipulation of the algorithms and decryption of the model with envelope encryption is made. The run phase executes the train image including all software requirements wrapped within the container to run the algorithm at one station. The third and last phase encrypts the train results and prepares the train for the departure. Only encrypted results are hosted centrally and must be decrypted locally.
Use Cases
We developed and customized our distributed learning platform for several use cases within the Medical Informatics Initiative.

We developed PHT-meDIC for distributed analysis of the Use Cases within DIFUTURE (project website)

Interoperable decentral access and analysis of genome data for the German Human Genome-Phenome Archive (project website)

The “Collaboration on Rare Diseases” aim is to improve care and research in the field of rare diseases. This is a joint project of the four consortia of the MII, in which numerous German university hospitals and partner institutions are involved (project website)

The “POLypharmazie, Arzneimittelwechselwirkungen, Risiken” use case encompasses all four consortia of the Medical Informatics Initiative and aims to contribute to the detection of health risks in patients with polymedication (project website)

The main aim is to develop machine learning models to classify the presence of leukodystrophies. Models will be trained using clinical, genetic and image data (MRI) from three centers for rare diseases (project website)